Understanding Network Scanning and Enumeration in Penetration Testing
Scanning and enumeration are the initial steps in a penetration tester’s methodology. This phase encompasses various tasks, such as identifying live hosts, IP addresses, open ports, services, and operating systems on the target network. It serves as reconnaissance, allowing testers to comprehend the network’s structure, uncover potential vulnerabilities, and evaluate its security posture.
Nmap: Your Reliable Network Mapper for Scanning and Discovery
Nmap, short for Network Mapper, is a renowned command-line tool in the cybersecurity realm. Cyber professionals frequently utilize it for network discovery and swift scanning across networks of all sizes. By sending specialized packets to target hosts and analyzing their responses, Nmap constructs a map of the network’s layout. Its insights play a pivotal role in the enumeration process. Remarkably, Nmap is compatible with Windows, Linux, and Mac OS, ensuring easy installation and usage.
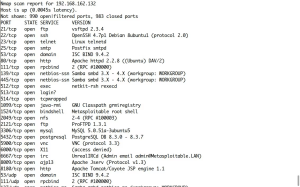
Nessus: Automated Vulnerability Scanning for Enhanced Security
Nessus, developed by Tenable Inc., stands as a popular automated vulnerability scanning and assessment tool. This solution aids security experts and researchers in identifying vulnerabilities within networks, systems, and applications. Organizations employ Nessus to proactively address potential weaknesses and bolster their security stance. With versions available for Linux, Windows, and MacOS, Nessus is user-friendly and accessible. While paid versions exist, the Nessus Essentials package offers comprehensive scanning capabilities.
Zenmap and Netdiscover: User-Friendly Alternatives for Efficient Scanning
Zenmap, the graphical user interface (GUI) version of Nmap, simplifies the visualization of scan results. Unlike the command-line interface (CLI) counterpart, Zenmap presents findings in an organized format, complete with a searchable database. This open-source tool is compatible with Linux, Windows, and MacOS. Users can save scan results and preferred commands for future reference.
Netdiscover serves as an active/passive reconnaissance tool, enabling network and IP address information gathering. Additionally, it inspects LAN traffic and identifies IP addresses. This command-line open-source tool is readily available on various Linux distributions.
Carrying Out a Good Penetration Test
The foundation of a successful penetration test rests on thorough information gathering and reconnaissance. This phase equips testers with a profound understanding of the target network. The more insights acquired about the system under scrutiny, the more effectively testers can execute precise and impactful assessments.
In conclusion, mastering the art of network scanning and enumeration is crucial for effective penetration testing. Nmap, Nessus, Zenmap, and Netdiscover stand out as valuable tools in this phase. Their combined capabilities empower testers to comprehensively assess network security and identify vulnerabilities that demand mitigation. By incorporating these tools into your penetration testing methodology, you can enhance your expertise, authoritativeness, and trustworthiness in the cybersecurity realm.