
Should You Buy a Used CPU? What Are the Risks?
When it comes to the world of technology, the decision between purchasing new or used items is a discussion that never seems to fade. This debate becomes particularly relevant when considering central processing units (CPUs), the beating hearts of computers that significantly impact a machine’s performance. In this article, we delve into the question of whether buying a used CPU is a wise choice and explore the associated risks that come with it.
Why Consider Buying a Used CPU?
CPUs are a fundamental component of all off-the-shelf computers; without them, these machines simply wouldn’t function. Given this ubiquity, it’s important to ask why one would even consider buying a used CPU in the first place.
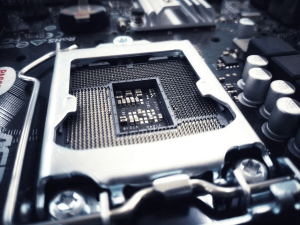
Performance Boost: Upgrading to a more powerful CPU is a straightforward and effective method to enhance a computer’s overall performance. A faster processor can lead to smoother multitasking, quicker application launches, and improved performance in resource-intensive tasks such as video editing or gaming.
Cost Savings: One of the primary motivations for opting for second-hand purchases is the potential for significant cost savings. Used CPUs often come at a fraction of the price of their brand-new counterparts. This appeal to budget-conscious consumers or those looking to build a powerful system without breaking the bank.
Compatibility: For individuals seeking to extend the lifespan of an older computer, a used CPU that is compatible with the existing motherboard can offer a practical solution. This can allow users to breathe new life into their machines without the need for a complete system overhaul.
So, on the surface, buying a used CPU seems like a no-brainer. It offers an economical way to improve a computer’s performance and can be especially appealing for those aiming to extend the life of older machines. But what potential risks lurk beneath the surface?
The Potential Risks of Used CPUs
As someone with over two decades of experience in building, repairing, and refurbishing computers, I can attest that CPUs have generally proven to be quite reliable components. In my experience, a used CPU is often more trustworthy than a used stick of RAM, for instance. However, that doesn’t mean there aren’t potential risks associated with used CPUs. Just like with any second-hand purchase, inherent risks exist, and CPUs are no exception.
Reliability: A CPU that has already endured heavy usage is more likely to fail. The challenge here lies in accurately determining the extent of its previous usage, which is often nearly impossible. While you can gauge the mileage of a used car from its dashboard, there are no similar mechanisms to reveal a CPU’s “mileage.”
Compatibility: Matching processors and motherboards is crucial. For example, the difference between Intel and AMD processors and motherboards involves distinct socket types like LGA and PGA. But this distinction is only the beginning; a CPU must also align with a compatible motherboard generation.
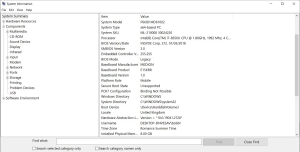
Misused Processors: CPUs that have been subjected to overclocking or overheating are more prone to failure. Overclocking, a common practice for enhancing performance, can, paradoxically, negatively impact a CPU’s longevity. Similarly, excessive heat resulting from insufficient heatsink compound or clogged cooling systems can lead to the same detrimental effect.
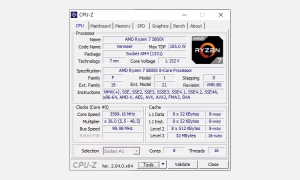
It’s important to note that despite these potential risks, numerous used CPUs function perfectly well and can provide considerable value. Nonetheless, understanding these risks and taking measures to mitigate them can contribute to a successful used CPU purchase, turning it into a smart decision rather than a costly mistake.
In the next section, we’ll explore what you should consider before purchasing a used CPU to ensure a successful transaction and minimize potential risks.





























